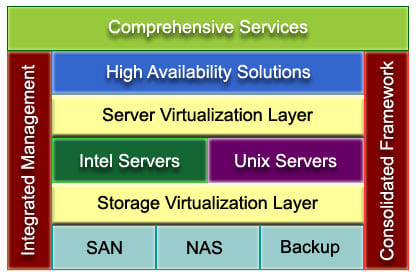
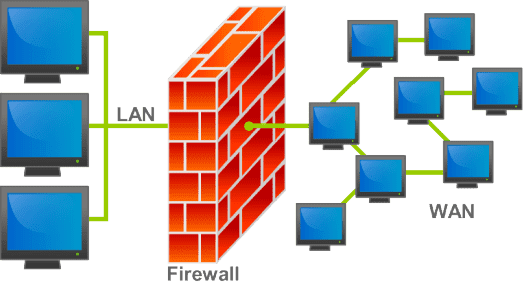
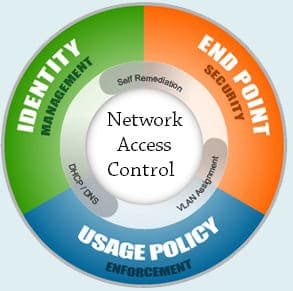
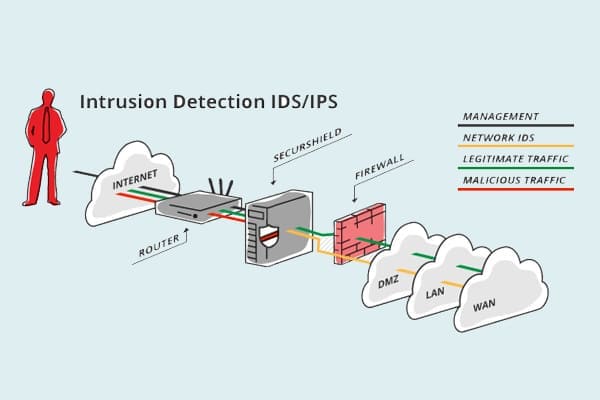
SNA specializes in IT solutions that bring businesses' visions to life. We analyze their priorities, existing IT systems, and anticipate future trends to craft enduring solutions. Our aim is to optimize IT spending, amplify business benefits, and deliver a robust ROI with the lowest total cost of ownership (TCO).
We excel in four core areas of Enterprise IT Solutions:
❖Network Infrastructure Solutions
❖Security Infrastructure Solutions
❖Software Infrastructure Solutions